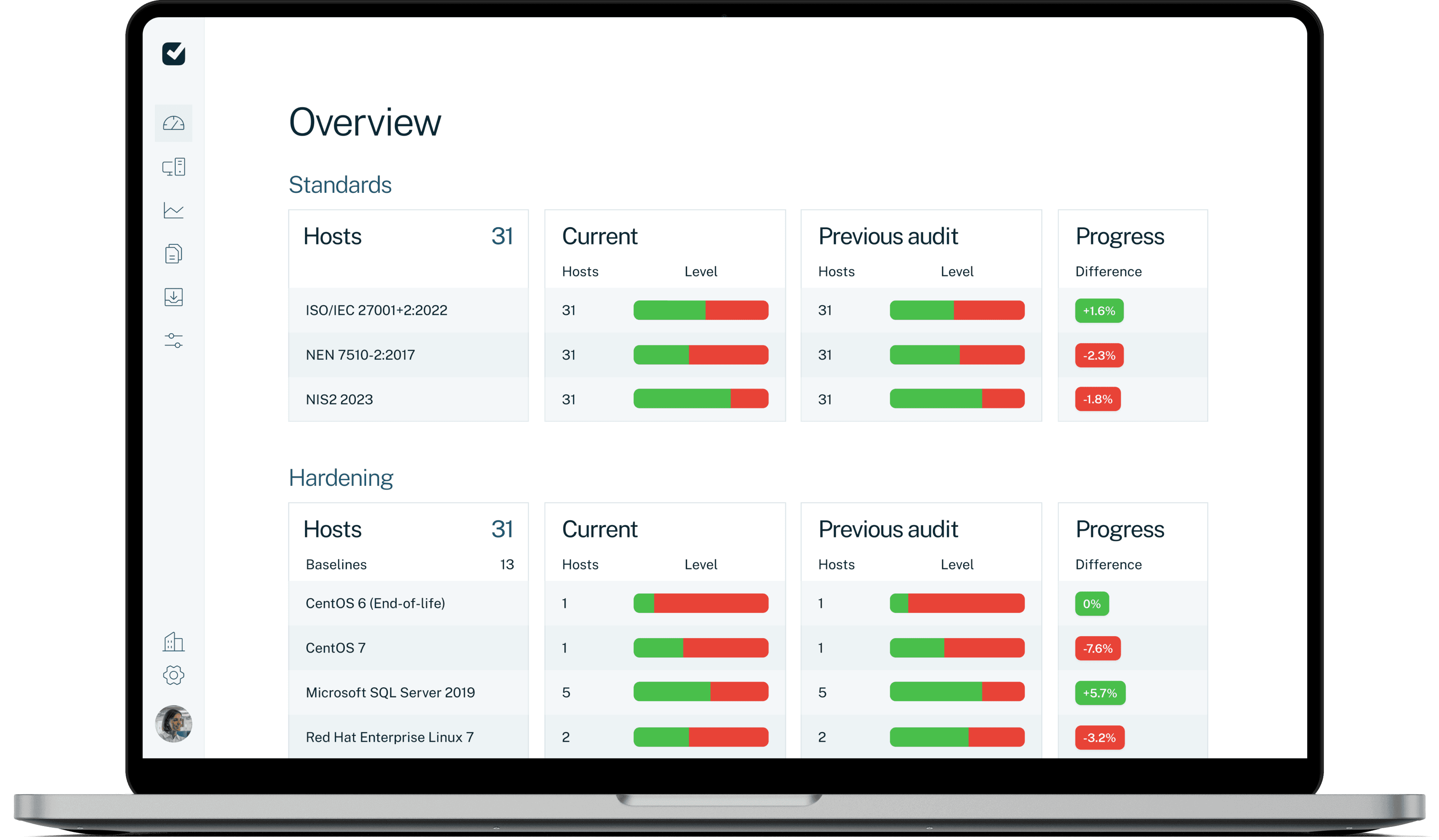
Self-hosted solution
Consolidated system insights in a single dashboard
The on-premise solution is ideal for customers with restrictions on transmitting client data over the internet and those seeking immediate overviews of multiple systems connected to their system.






One centralised view of all connected systems






Chosen by industry leaders for auditing solutions
Chosen by industry leaders for auditing solutions
Chosen by industry leaders for auditing solutions
Chosen by industry leaders for auditing solutions
Simple dashboard
Simple dashboard
Simple dashboard
Effortless system monitoring for regulatory compliance
Effortless system monitoring for regulatory compliance
Effortless system monitoring for regulatory compliance
Our user-friendly dashboard offers direct insights into multiple systems, allowing seamless integration while ensuring regulatory compliance. It is suitable for internal departments, accountants, and IT auditors.
Our user-friendly dashboard offers direct insights into multiple systems, allowing seamless integration while ensuring regulatory compliance. It is suitable for internal departments, accountants, and IT auditors.
Our user-friendly dashboard offers direct insights into multiple systems, allowing seamless integration while ensuring regulatory compliance. It is suitable for internal departments, accountants, and IT auditors.
Dashboard with direct insights
Our dashboard offers a centralised view of connected systems, showing key IT controls like antivirus status, updates & vulnerabilities, logical access, and hardening measures.

Dashboard with direct insights
Our dashboard offers a centralised view of connected systems, showing key IT controls like antivirus status, updates & vulnerabilities, logical access, and hardening measures.

Dashboard with direct insights
Our dashboard offers a centralised view of connected systems, showing key IT controls like antivirus status, updates & vulnerabilities, logical access, and hardening measures.

Dashboard with direct insights
Our dashboard offers a centralised view of connected systems, showing key IT controls like antivirus status, updates & vulnerabilities, logical access, and hardening measures.

For small and large numbers of servers and PCs
Seamlessly integrate and manage multiple systems in a consolidated view of all connected systems.

For small and large numbers of servers and PCs
Seamlessly integrate and manage multiple systems in a consolidated view of all connected systems.

For small and large numbers of servers and PCs
Seamlessly integrate and manage multiple systems in a consolidated view of all connected systems.

For small and large numbers of servers and PCs
Seamlessly integrate and manage multiple systems in a consolidated view of all connected systems.

Apply filters on your data
Ensure a personalised view of all connected systems for effective monitoring and reporting to your clients.

Apply filters on your data
Ensure a personalised view of all connected systems for effective monitoring and reporting to your clients.

Apply filters on your data
Ensure a personalised view of all connected systems for effective monitoring and reporting to your clients.

Apply filters on your data
Ensure a personalised view of all connected systems for effective monitoring and reporting to your clients.

Check regulations and compliance
Ensure compliance with key regulations to establish a secure framework for monitoring connected systems.

Check regulations and compliance
Ensure compliance with key regulations to establish a secure framework for monitoring connected systems.

Check regulations and compliance
Ensure compliance with key regulations to establish a secure framework for monitoring connected systems.

Check regulations and compliance
Ensure compliance with key regulations to establish a secure framework for monitoring connected systems.

Compliance & regulations
Ensuring cybersecurity and data protection
NIS2
ISO 27002
NIST
ISA 315
CIS v8
Compliance & regulations
Ensuring cybersecurity and data protection
NIS2
ISO 27002
NIST
ISA 315
CIS v8
Compliance & regulations
Ensuring cybersecurity and data protection
NIS2
ISO 27002
NIST
ISA 315
CIS v8
Compliance & regulations
Ensuring cybersecurity and data protection
NIS2
ISO 27002
NIST
ISA 315
CIS v8
Industries
Solutions for different professionals
Industries
Solutions for different professionals
Industries
Solutions for different professionals
Industries
Solutions for different professionals
IT audit firms & freelancers

Learn more
➔
IT & compliance departments

Learn more
➔
Accountant firms

Learn more
➔
IT audit firms & freelancers

Learn more
➔
IT & compliance departments

Learn more
➔
Accountant firms

Learn more
➔
IT audit firms & freelancers

Learn more
➔
IT & compliance departments

Learn more
➔
Accountant firms

Learn more
➔
IT audit firms & freelancers

Learn more
➔
IT & compliance departments

Learn more
➔
Accountant firms

Learn more
➔
Create reports easily
Tailored audit reports
Let Easy2audit handle the tedious and time-consuming tasks. We gather data from your systems, organise it, and present it in user-friendly reports, streamlining your auditing process.
IT-audit summary
Outline critical security measures of an operating system, centred on key ITGCs. Cover local account policies, including password policies and lockout protocols, along with additional hardening settings.
View sample report
Active Directory & EntraID
Crafted with input from IT auditors across various firms, both small and large, these reports display the rights, privileges, and various other security-related attributes of AD users.
View sample report
SQL
Databases harbor extensive and vital data, necessitating an analysis of user activity, privileges, and behaviour to safeguard against misuse of accounts.
View sample report
System configurations (hardening)
Default operating system configurations prioritise usability over security, leaving vulnerabilities for cybercriminals. Adjusting these configurations is a critical cybersecurity measure.
View sample report
Create reports easily
Tailored audit reports
Let Easy2audit handle the tedious and time-consuming tasks. We gather data from your systems, organise it, and present it in user-friendly reports, streamlining your auditing process.
IT-audit summary
Outline critical security measures of an operating system, centred on key ITGCs. Cover local account policies, including password policies and lockout protocols, along with additional hardening settings.
View sample report
Active Directory & EntraID
Crafted with input from IT auditors across various firms, both small and large, these reports display the rights, privileges, and various other security-related attributes of AD users.
View sample report
SQL
Databases harbor extensive and vital data, necessitating an analysis of user activity, privileges, and behaviour to safeguard against misuse of accounts.
View sample report
System configurations (hardening)
Default operating system configurations prioritise usability over security, leaving vulnerabilities for cybercriminals. Adjusting these configurations is a critical cybersecurity measure.
View sample report
Create reports easily
Tailored audit reports
Let Easy2audit handle the tedious and time-consuming tasks. We gather data from your systems, organise it, and present it in user-friendly reports, streamlining your auditing process.
IT-audit summary
Outline critical security measures of an operating system, centred on key ITGCs. Cover local account policies, including password policies and lockout protocols, along with additional hardening settings.
View sample report
Active Directory & EntraID
Crafted with input from IT auditors across various firms, both small and large, these reports display the rights, privileges, and various other security-related attributes of AD users.
View sample report
SQL
Databases harbor extensive and vital data, necessitating an analysis of user activity, privileges, and behaviour to safeguard against misuse of accounts.
View sample report
System configurations (hardening)
Default operating system configurations prioritise usability over security, leaving vulnerabilities for cybercriminals. Adjusting these configurations is a critical cybersecurity measure.
View sample report
Create reports easily
Tailored audit reports
Let Easy2audit handle the tedious and time-consuming tasks. We gather data from your systems, organise it, and present it in user-friendly reports, streamlining your auditing process.
IT-audits summary reports
Outline critical security measures of an operating system, centred on key ITGCs. Cover local account policies, including password policies and lockout protocols, along with additional hardening settings.
View sample report
Active Directory reports
Crafted with input from IT auditors across various firms, both small and large, these reports display the rights, privileges, and various other security-related attributes of AD users.
View sample report
SQL reports
Databases harbor extensive and vital data, necessitating an analysis of user activity, privileges, and behaviour to safeguard against misuse of accounts.
View sample report
System configuration reports
Default operating system configurations prioritise usability over security, leaving vulnerabilities for cybercriminals. Adjusting these configurations is a critical cybersecurity measure.
View sample report
IT-audits summary reports
Outline critical security measures of an operating system, centred on key ITGCs. Cover local account policies, including password policies and lockout protocols, along with additional hardening settings.
View sample report
Active Directory reports
Crafted with input from IT auditors across various firms, both small and large, these reports display the rights, privileges, and various other security-related attributes of AD users.
View sample report
SQL reports
Databases harbor extensive and vital data, necessitating an analysis of user activity, privileges, and behaviour to safeguard against misuse of accounts.
View sample report
System configuration reports
Default operating system configurations prioritise usability over security, leaving vulnerabilities for cybercriminals. Adjusting these configurations is a critical cybersecurity measure.
View sample report
IT-audits summary reports
Outline critical security measures of an operating system, centred on key ITGCs. Cover local account policies, including password policies and lockout protocols, along with additional hardening settings.
View sample report
Active Directory reports
Crafted with input from IT auditors across various firms, both small and large, these reports display the rights, privileges, and various other security-related attributes of AD users.
View sample report
SQL reports
Databases harbor extensive and vital data, necessitating an analysis of user activity, privileges, and behaviour to safeguard against misuse of accounts.
View sample report
System configuration reports
Default operating system configurations prioritise usability over security, leaving vulnerabilities for cybercriminals. Adjusting these configurations is a critical cybersecurity measure.
View sample report
IT-audits summary reports
Outline critical security measures of an operating system, centred on key ITGCs. Cover local account policies, including password policies and lockout protocols, along with additional hardening settings.
View sample report
Active Directory reports
Crafted with input from IT auditors across various firms, both small and large, these reports display the rights, privileges, and various other security-related attributes of AD users.
View sample report
SQL reports
Databases harbor extensive and vital data, necessitating an analysis of user activity, privileges, and behaviour to safeguard against misuse of accounts.
View sample report
System configuration reports
Default operating system configurations prioritise usability over security, leaving vulnerabilities for cybercriminals. Adjusting these configurations is a critical cybersecurity measure.
View sample report
Impact of using Easy2audit
Time-saving
Our solution saves you and your clients valuable time, allowing you to complete audits in a fraction of the time it would take to do them manually.
Data privacy
Data uploaded to our system is immediately deleted after the reports have been generated, ensuring privacy and security for both you and your clients.
Detailed insights
Gain detailed direct insights in a personalised dashboard view, allowing you to see key IT controls.
One system
Access all your clients’ systems in one dashboard, filtering based on your requirements. You can even assign employees to only have access to their own clients.
Self-hosted
Developed to meet organisational requirements for automating small and large-scale business systems.
Easily accessible
Access our dashboard from anywhere and generate IT reports effortlessly in just three simple steps within the environment.
Partnerships we are proud of


Impact of using Easy2audit
Time-saving
Our solution saves you and your clients valuable time, allowing you to complete audits in a fraction of the time it would take to do them manually.
Data privacy
Data uploaded to our system is immediately deleted after the reports have been generated, ensuring privacy and security for both you and your clients.
Detailed insights
Gain detailed direct insights in a personalised dashboard view, allowing you to see key IT controls.
One system
Access all your clients’ systems in one dashboard, filtering based on your requirements. You can even assign employees to only have access to their own clients.
Self-hosted
Developed to meet organisational requirements for automating small and large-scale business systems.
Easily accessible
Access our dashboard from anywhere and generate IT reports effortlessly in just three simple steps within the environment.
Partnerships we are proud of


Impact of using Easy2audit
Time-saving
Our solution saves you and your clients valuable time, allowing you to complete audits in a fraction of the time it would take to do them manually.
Data privacy
Data uploaded to our system is immediately deleted after the reports have been generated, ensuring privacy and security for both you and your clients.
Detailed insights
Gain detailed direct insights in a personalised dashboard view, allowing you to see key IT controls.
One system
Access all your clients’ systems in one dashboard, filtering based on your requirements. You can even assign employees to only have access to their own clients.
Self-hosted
Developed to meet organisational requirements for automating small and large-scale business systems.
Easily accessible
Access our dashboard from anywhere and generate IT reports effortlessly in just three simple steps within the environment.
Partnerships we are proud of


Impact of using Easy2audit
One system
Access all your clients’ systems in one dashboard, filtering based on your requirements. You can even assign employees to only have access to their own clients.
Self-hosted
Developed to meet organisational requirements for automating small and large-scale business systems.
Easily accessible
Access our dashboard from anywhere and generate IT reports effortlessly in just three simple steps within the environment.
Time-saving
Our solution saves you and your clients valuable time, allowing you to complete audits in a fraction of the time it would take to do them manually.
Detailed insights
Gain detailed direct insights in a personalised dashboard view, allowing you to see key IT controls.
One system
Access all your clients’ systems in one dashboard, filtering based on your requirements. You can even assign employees to only have access to their own clients.
Self-hosted
Developed to meet organisational requirements for automating small and large-scale business systems.
Easily accessible
Access our dashboard from anywhere and generate IT reports effortlessly in just three simple steps within the environment.
Time-saving
Our solution saves you and your clients valuable time, allowing you to complete audits in a fraction of the time it would take to do them manually.
Detailed insights
Gain detailed direct insights in a personalised dashboard view, allowing you to see key IT controls.
One system
Access all your clients’ systems in one dashboard, filtering based on your requirements. You can even assign employees to only have access to their own clients.
Self-hosted
Developed to meet organisational requirements for automating small and large-scale business systems.
Easily accessible
Access our dashboard from anywhere and generate IT reports effortlessly in just three simple steps within the environment.
Time-saving
Our solution saves you and your clients valuable time, allowing you to complete audits in a fraction of the time it would take to do them manually.
Detailed insights
Gain detailed direct insights in a personalised dashboard view, allowing you to see key IT controls.
One system
Access all your clients’ systems in one dashboard, filtering based on your requirements. You can even assign employees to only have access to their own clients.
Self-hosted
Developed to meet organisational requirements for automating small and large-scale business systems.
Easily accessible
Access our dashboard from anywhere and generate IT reports effortlessly in just three simple steps within the environment.
Time-saving
Our solution saves you and your clients valuable time, allowing you to complete audits in a fraction of the time it would take to do them manually.
Detailed insights
Gain detailed direct insights in a personalised dashboard view, allowing you to see key IT controls.
Partnerships we are proud of


What our customers say
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
What our customers say
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
What our customers say
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
What our customers say
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
Frequently asked questions
Everything you need to know about the product and billing.
Easy2audit script
Easy2audit uses scripts. What kind of scripts are they?
The Easy2audit scripts are developed in-house and are specifically designed to read configuration settings.
Is there one script or multiple scripts?
Will the Easy2audit scripts impact the stability of my server?
How does the script read the settings?
What permissions do the scripts need to be run?
Do the scripts change the configuration settings?
Do the scripts create temporary files?
Where do the scripts save the results?
Can I view the scripts before I run them?
IT General Controls (ITGC)
What are IT General Controls (ITGC)?
Which IT General Controls (ITGC) does Easy2Audit address?
Frequently asked questions
Everything you need to know about the product and billing.
Easy2audit script
Easy2audit uses scripts. What kind of scripts are they?
The Easy2audit scripts are developed in-house and are specifically designed to read configuration settings.
Is there one script or multiple scripts?
Will the Easy2audit scripts impact the stability of my server?
How does the script read the settings?
What permissions do the scripts need to be run?
Do the scripts change the configuration settings?
Do the scripts create temporary files?
Where do the scripts save the results?
Can I view the scripts before I run them?
IT General Controls (ITGC)
What are IT General Controls (ITGC)?
Which IT General Controls (ITGC) does Easy2Audit address?
Frequently asked questions
Everything you need to know about the product and billing.
Easy2audit script
Easy2audit uses scripts. What kind of scripts are they?
The Easy2audit scripts are developed in-house and are specifically designed to read configuration settings.
Is there one script or multiple scripts?
Will the Easy2audit scripts impact the stability of my server?
How does the script read the settings?
What permissions do the scripts need to be run?
Do the scripts change the configuration settings?
Do the scripts create temporary files?
Where do the scripts save the results?
Can I view the scripts before I run them?
IT General Controls (ITGC)
What are IT General Controls (ITGC)?
Which IT General Controls (ITGC) does Easy2Audit address?
Frequently asked questions
Everything you need to know about the product and billing.
Easy2audit script
Easy2audit uses scripts. What kind of scripts are they?
The Easy2audit scripts are developed in-house and are specifically designed to read configuration settings.
Is there one script or multiple scripts?
Will the Easy2audit scripts impact the stability of my server?
How does the script read the settings?
What permissions do the scripts need to be run?
Do the scripts change the configuration settings?
Do the scripts create temporary files?
Where do the scripts save the results?
Can I view the scripts before I run them?
IT General Controls (ITGC)
What are IT General Controls (ITGC)?
Which IT General Controls (ITGC) does Easy2Audit address?