Industries
Accounting firms
Accurate figures are crucial for financial audits. Easy2audit provides IT report insights, enabling accountants to rely on objective data instead of clients’ systems reports. This enhances financial audits and facilitates information sharing with other professional IT auditors.
Generate summarised IT audit reports
Generate summarised IT audit reports
Generate summarised IT audit reports



1 source
of truth
1 source
of truth
1 source
of truth
8 hours
saved per system
8 hours
saved per system
8 hours
saved per system
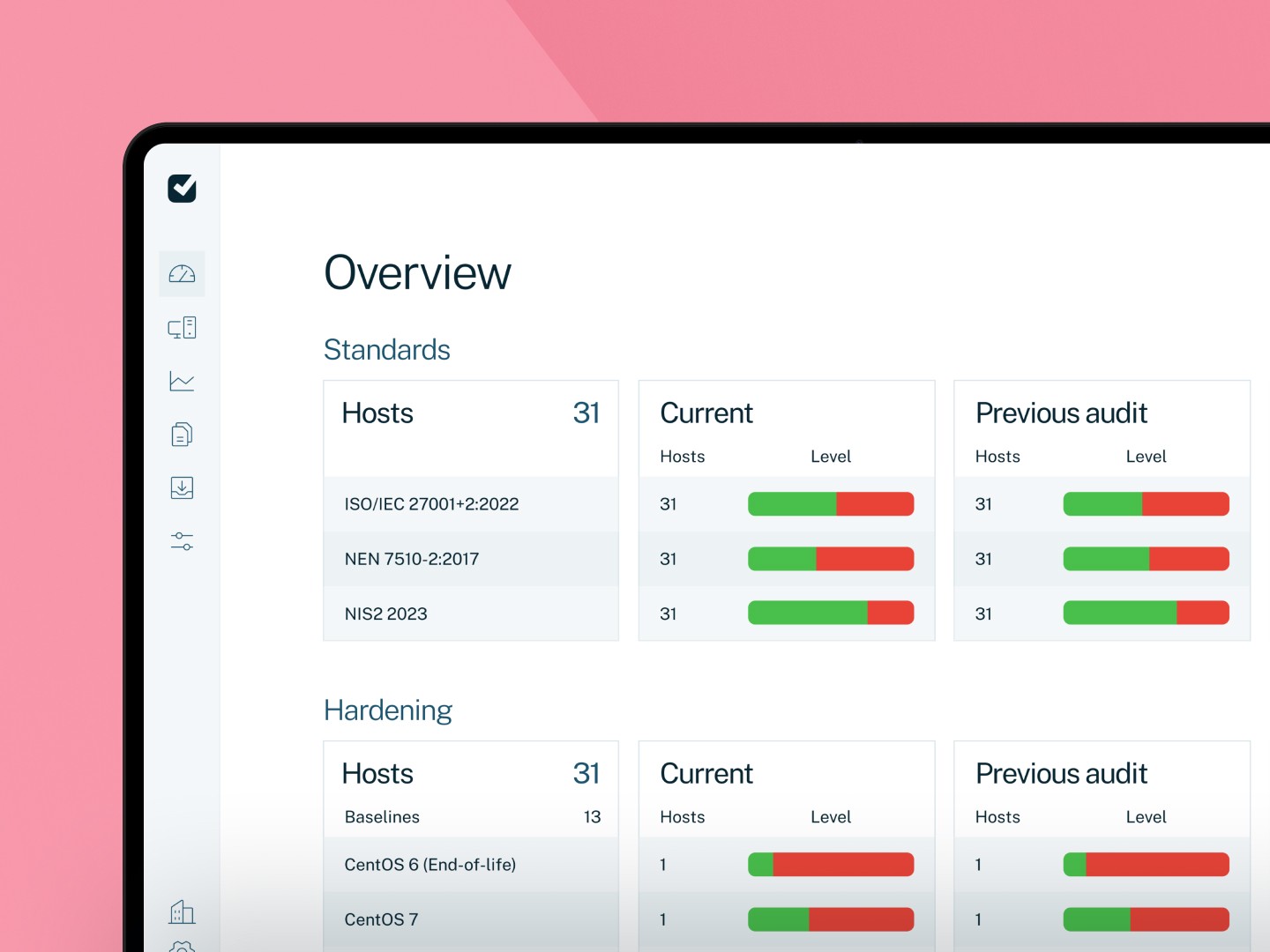
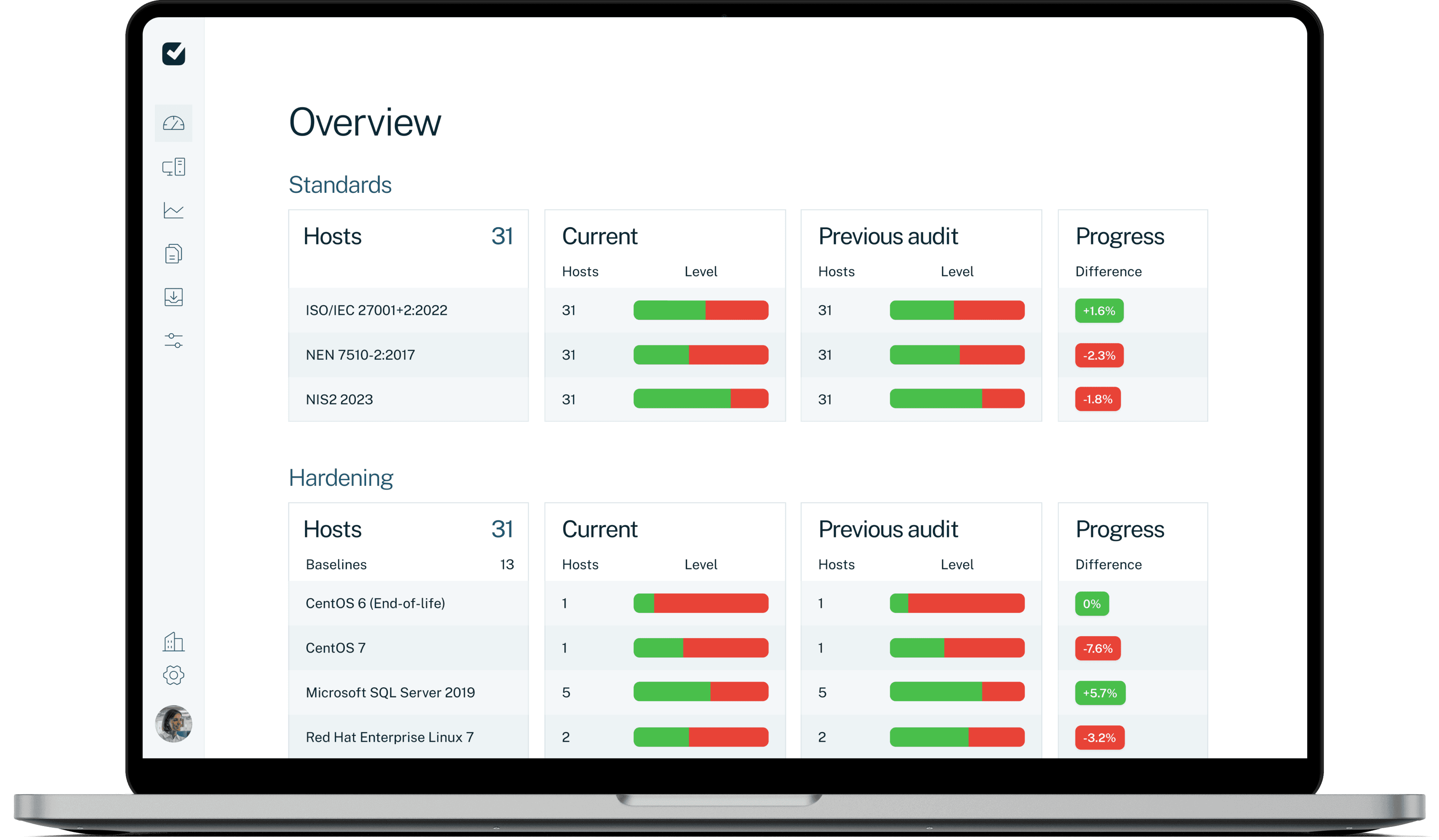
Ensure security and compliance to support your financial audits
Rely on objective data in your financial auditing process.
IT controls insights
Gain valuable insights into IT controls and their effectiveness, crucial for ensuring financial data integrity.
Integrated approach
Leverage a unified method to assess IT-related financial risks, enhancing the quality of your financial audits.
ISA 315 compliance
Easy2audit adheres to the ISA 315 standards, offering professional guidelines to streamline your audit processes according to this international standard.
85% of the passwords are set up securely

Ensure security and compliance to support your financial audits
Rely on objective data in your financial auditing process.
IT controls insights
Gain valuable insights into IT controls and their effectiveness, crucial for ensuring financial data integrity.
Integrated approach
Leverage a unified method to assess IT-related financial risks, enhancing the quality of your financial audits.
ISA 315 compliance
Easy2audit adheres to the ISA 315 standards, offering professional guidelines to streamline your audit processes according to this international standard.
85% of the passwords are set up securely

Ensure security and compliance to support your financial audits
Rely on objective data in your financial auditing process.
IT controls insights
Gain valuable insights into IT controls and their effectiveness, crucial for ensuring financial data integrity.
Integrated approach
Leverage a unified method to assess IT-related financial risks, enhancing the quality of your financial audits.
ISA 315 compliance
Easy2audit adheres to the ISA 315 standards, offering professional guidelines to streamline your audit processes according to this international standard.
85% of the passwords are set up securely

Gain direct insights into your client’s Active Directory
Easily monitor essential IT controls and gain valuable insights into audit rights, privileges, and other key attributes.rols effortlessly and gain valuable insights.
9 enterprise adminstrators are active
26% of the users inactive
2935 total users

Antivirus
Antivirus software: Ensure it's active and up-to-date across all systems.
Updates & Vulnerabilities
Updates (Patching) & Vulnerabilities (CVEs): Stay informed about OS updates and potential vulnerabilities.
Logical access
Logical access control & Authorizations: Access detailed insights into Active Directory, SQL User details, and Fine-Grained Policies.
Hardening
Security Configurations (Hardening): Assess and enhance security configurations for optimal protection.
Gain direct insights into your client’s Active Directory
Easily monitor essential IT controls and gain valuable insights into audit rights, privileges, and other key attributes.rols effortlessly and gain valuable insights.
9 enterprise adminstrators are active

Antivirus
Antivirus software: Ensure it's active and up-to-date across all systems.
Updates & Vulnerabilities
Updates (Patching) & Vulnerabilities (CVEs): Stay informed about OS updates and potential vulnerabilities.
Logical access
Logical access control & Authorizations: Access detailed insights into Active Directory, SQL User details, and Fine-Grained Policies.
Hardening
Security Configurations (Hardening): Assess and enhance security configurations for optimal protection.
Gain direct insights into your client’s Active Directory
Easily monitor essential IT controls and gain valuable insights into audit rights, privileges, and other key attributes.rols effortlessly and gain valuable insights.
9 enterprise adminstrators are active
26% of the users inactive
2935 total users

Antivirus
Antivirus software: Ensure it's active and up-to-date across all systems.
Updates & Vulnerabilities
Updates (Patching) & Vulnerabilities (CVEs): Stay informed about OS updates and potential vulnerabilities.
Logical access
Logical access control & Authorizations: Access detailed insights into Active Directory, SQL User details, and Fine-Grained Policies.
Hardening
Security Configurations (Hardening): Assess and enhance security configurations for optimal protection.
Independence without Debate
What matters most to auditors
Easy2audit is designed to fully respect the independent role of the external auditor. The tool strictly measures and reports and does not perform any configuration changes or operational actions within client environments.
Reliable and reproducible audit evidence
Measurements are consistent, repeatable, and verifiable. Findings remain traceable over time and across environments, which is essential for reviews and assurance engagements.
Transparency in methodology and technology
Easy2audit does not operate as a black box. The scripts used and the resulting output files are transparent and can be clearly explained to clients, reviewers, and regulators.
Efficiency without loss of quality
Easy2audit does not operate as a black box. The scripts used and the resulting output files are transparent and can be clearly explained to clients, reviewers, and regulators.
Alignment with widely used standards
Easy2audit supports audits based on, among others, NIS2, ISO 27001/27002, BIO, NEN 7510, DORA, and CIS Benchmarks, with a focus on the actual technical configuration of systems.
Independence without Debate
What matters most to auditors
Easy2audit is designed to fully respect the independent role of the external auditor. The tool strictly measures and reports and does not perform any configuration changes or operational actions within client environments.
Reliable and reproducible audit evidence
Measurements are consistent, repeatable, and verifiable. Findings remain traceable over time and across environments, which is essential for reviews and assurance engagements.
Transparency in methodology and technology
Easy2audit does not operate as a black box. The scripts used and the resulting output files are transparent and can be clearly explained to clients, reviewers, and regulators.
Efficiency without loss of quality
Easy2audit does not operate as a black box. The scripts used and the resulting output files are transparent and can be clearly explained to clients, reviewers, and regulators.
Alignment with widely used standards
Easy2audit supports audits based on, among others, NIS2, ISO 27001/27002, BIO, NEN 7510, DORA, and CIS Benchmarks, with a focus on the actual technical configuration of systems.

Independence without Debate
What matters most to auditors
Easy2audit is designed to fully respect the independent role of the external auditor. The tool strictly measures and reports and does not perform any configuration changes or operational actions within client environments.
Reliable and reproducible audit evidence
Measurements are consistent, repeatable, and verifiable. Findings remain traceable over time and across environments, which is essential for reviews and assurance engagements.
Transparency in methodology and technology
Easy2audit does not operate as a black box. The scripts used and the resulting output files are transparent and can be clearly explained to clients, reviewers, and regulators.
Efficiency without loss of quality
Easy2audit does not operate as a black box. The scripts used and the resulting output files are transparent and can be clearly explained to clients, reviewers, and regulators.
Alignment with widely used standards
Easy2audit supports audits based on, among others, NIS2, ISO 27001/27002, BIO, NEN 7510, DORA, and CIS Benchmarks, with a focus on the actual technical configuration of systems.

Create reports easily
IT reports for data accuracy
Access IT reports aligned with your accounting needs. These reports ensure the secure configuration of digital systems and provide crucial insights to support you in financial audits.
IT-audit summary
Outline critical security measures of an operating system, centred on key ITGCs. Cover local account policies, including password policies and lockout protocols, along with additional hardening settings.
View sample report
Active Directory & EntraID
Crafted with input from IT auditors across various firms, both small and large, these reports display the rights, privileges, and various other security-related attributes of AD users.
View sample report
SQL
Databases harbor extensive and vital data, necessitating an analysis of user activity, privileges, and behaviour to safeguard against misuse of accounts.
View sample report
System configurations (hardening)
Default operating system configurations prioritise usability over security, leaving vulnerabilities for cybercriminals. Adjusting these configurations is a critical cybersecurity measure.
View sample report
Create reports easily
IT reports for data accuracy
Access IT reports aligned with your accounting needs. These reports ensure the secure configuration of digital systems and provide crucial insights to support you in financial audits.
IT-audit summary
Outline critical security measures of an operating system, centred on key ITGCs. Cover local account policies, including password policies and lockout protocols, along with additional hardening settings.
View sample report
Active Directory & EntraID
Crafted with input from IT auditors across various firms, both small and large, these reports display the rights, privileges, and various other security-related attributes of AD users.
View sample report
SQL
Databases harbor extensive and vital data, necessitating an analysis of user activity, privileges, and behaviour to safeguard against misuse of accounts.
View sample report
System configurations (hardening)
Default operating system configurations prioritise usability over security, leaving vulnerabilities for cybercriminals. Adjusting these configurations is a critical cybersecurity measure.
View sample report
Create reports easily
IT reports for data accuracy
Access IT reports aligned with your accounting needs. These reports ensure the secure configuration of digital systems and provide crucial insights to support you in financial audits.
IT-audit summary
Outline critical security measures of an operating system, centred on key ITGCs. Cover local account policies, including password policies and lockout protocols, along with additional hardening settings.
View sample report
Active Directory & EntraID
Crafted with input from IT auditors across various firms, both small and large, these reports display the rights, privileges, and various other security-related attributes of AD users.
View sample report
SQL
Databases harbor extensive and vital data, necessitating an analysis of user activity, privileges, and behaviour to safeguard against misuse of accounts.
View sample report
System configurations (hardening)
Default operating system configurations prioritise usability over security, leaving vulnerabilities for cybercriminals. Adjusting these configurations is a critical cybersecurity measure.
View sample report
Solutions
Customised solutions for efficient auditing and precise remediation
We offer customised solutions to support your auditing process, providing detailed insights tailored to your specific needs.
Maximize your cyber security with system hardening
Benchmark your systems against standards like NIST, CIS, and ISO for detailed controls, explanations, and mitigation recommendations. All in one single overview.

Identify which user accounts need to be removed or have unused functions disabled.
View the secure values assigned to security settings.
Identify default passwords and update them to improve security.
Solutions
Customised solutions for efficient auditing and precise remediation
We offer customised solutions to support your auditing process, providing detailed insights tailored to your specific needs.
Maximize your cyber security with system hardening
Benchmark your systems against standards like NIST, CIS, and ISO for detailed controls, explanations, and mitigation recommendations. All in one single overview.

Identify which user accounts need to be removed or have unused functions disabled.
View the secure values assigned to security settings.
Identify default passwords and update them to improve security.
Solutions
Customised solutions for efficient auditing and precise remediation
We offer customised solutions to support your auditing process, providing detailed insights tailored to your specific needs.
Maximize your cyber security with system hardening
Benchmark your systems against standards like NIST, CIS, and ISO for detailed controls, explanations, and mitigation recommendations. All in one single overview.

Identify which user accounts need to be removed or have unused functions disabled.
View the secure values assigned to security settings.
Identify default passwords and update them to improve security.
Impact of using Easy2audit
Professional guidelines
Access professional memorandum and working papers in line with ISA 315, enhancing your audit workflow.
Time efficiency
Reduce the time spent on manual correlations between IT security posture and financial risks.
Data accuracy
Ensure higher accuracy in financial reporting through detailed IT control assessments.
Partnerships we are proud of


Impact of using Easy2audit
Professional guidelines
Access professional memorandum and working papers in line with ISA 315, enhancing your audit workflow.
Time efficiency
Reduce the time spent on manual correlations between IT security posture and financial risks.
Data accuracy
Ensure higher accuracy in financial reporting through detailed IT control assessments.
Partnerships we are proud of


Impact of using Easy2audit
Professional guidelines
Access professional memorandum and working papers in line with ISA 315, enhancing your audit workflow.
Time efficiency
Reduce the time spent on manual correlations between IT security posture and financial risks.
Data accuracy
Ensure higher accuracy in financial reporting through detailed IT control assessments.
Partnerships we are proud of


What our customers say
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
What our customers say
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
What our customers say
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
“Getting all the right data from our clients used to take a lot of time for all parties involved. With Easy2audit, the process is so quick and easy that our clients are now happy to cooperate. The full transparency of the scripts and output and the fact that there’s no need for installations are great features too.”

Robert Johan RE CISSP
SOLL-IT
"Easy2audit has assisted us for many years in efficiently organizing and monitoring our hardening according to the BIO standard, and thereby taking our digital security to a higher level."

Johannes Grimmerink
DOWR (Municipalities of Deventer, Olst-Wijhe & Raalte)
“The extensive system hardening reports and Active Directory reports are extremely useful, and hard to find anywhere else. The application is incredibly easy to use and saves me loads of time.”

Mark Langenakker
AKL Support
Resources
The latest insights
Discover the latest industry news, interviews, and other insightful content.
Resources
The latest insights
Discover the latest industry news, interviews, and other insightful content.
Resources
The latest insights
Discover the latest industry news, interviews, and other insightful content.
Frequently asked questions
Everything you need to know about the product and billing.
Easy2audit script
Easy2audit uses scripts. What kind of scripts are they?
The Easy2audit scripts are developed in-house and are specifically designed to read configuration settings.
Is there one script or multiple scripts?
Will the Easy2audit scripts impact the stability of my server?
How does the script read the settings?
What permissions do the scripts need to be run?
Do the scripts change the configuration settings?
Do the scripts create temporary files?
Where do the scripts save the results?
Can I view the scripts before I run them?
IT General Controls (ITGC)
What are IT General Controls (ITGC)?
Which IT General Controls (ITGC) does Easy2Audit address?
Frequently asked questions
Everything you need to know about the product and billing.
Easy2audit script
Easy2audit uses scripts. What kind of scripts are they?
The Easy2audit scripts are developed in-house and are specifically designed to read configuration settings.
Is there one script or multiple scripts?
Will the Easy2audit scripts impact the stability of my server?
How does the script read the settings?
What permissions do the scripts need to be run?
Do the scripts change the configuration settings?
Do the scripts create temporary files?
Where do the scripts save the results?
Can I view the scripts before I run them?
IT General Controls (ITGC)
What are IT General Controls (ITGC)?
Which IT General Controls (ITGC) does Easy2Audit address?
Frequently asked questions
Everything you need to know about the product and billing.
Easy2audit script
Easy2audit uses scripts. What kind of scripts are they?
The Easy2audit scripts are developed in-house and are specifically designed to read configuration settings.
Is there one script or multiple scripts?
Will the Easy2audit scripts impact the stability of my server?
How does the script read the settings?
What permissions do the scripts need to be run?
Do the scripts change the configuration settings?
Do the scripts create temporary files?
Where do the scripts save the results?
Can I view the scripts before I run them?
IT General Controls (ITGC)
What are IT General Controls (ITGC)?
Which IT General Controls (ITGC) does Easy2Audit address?
Ready to optimise your financial audits?
Prioritise accuracy

Etienne Schraven
Director

Ready to optimise your financial audits?
Prioritise accuracy

Etienne Schraven
Director